If you are running Vagrant on a Windows host, connecting to the Vagrant managed machines is not very straight forward. This is so because Windows does not natively support SSH. I usually use one of these options to interact with my Vagrant VMs from Windows:
- Get SSH for Windows
You can do this by installing Cygwin or Git for Windows. After installation, set the location of ssh.exe in your PATH Environment variable. Lastly, just type “vagrant ssh <<machine name or IP>>” from the Windows command prompt. - Use WinSCP
WinSCP is useful to transfer files between your host and the VMs. Of course, you can also use Shared Folders feature of VirtualBox which is also easily configurable through Vagrant. - Use an SSH Client like PuTTY --> the focus of this article.
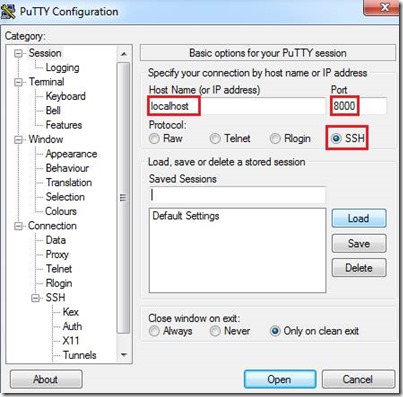
Decide on the Host Name and the Port
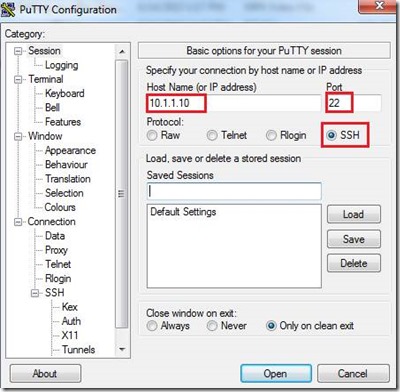
When using PuTTY, you can either connect directly to IP address of the VM or through the localhost (via port forwarding):Option 1 - Login with username/password
Once you connect, you will get the login prompt. The default username/password is vagrant/vagrant
Option 2 - Login with SSH Keys
An easier way to connect than using passwords is using SSH keys. So how does this work?
When you manage a VM through Vagrant, it automatically does the following things on the host:
- Create a public-private key pairs
- Copy the keys into the ~vagrant/.ssh directory
- Adds the public key to the ~vagrant/.ssh/authorized_keys file
The private key generated is then copied on to the local machine to enable automatic connection through SSH. In this section we’ll see how to find out the location of the VM’s private key in your host and then use it to connect to the VM via PuTTY.
Step 1 - Identify the location of Vagrant’s private key for your VM
To find out the location of the private key go to the host directory containing your VagrantFile and type “vagrant ssh-config”. This command will give you the entire SSH configuration.You will get the private key location in the “IdentityFile” field. To run this command you need the VM to be up and running.
Alternately, you can just drill down in to the directory containing the VagrantFile and locate the file named “private_key”. For example, in my case the VagrantFile is present in “F:\Virtual Machines\ELK1” directory. I found the private key file in “F:\Virtual Machines\ELK1\.vagrant\machines\logstash-server\virtualbox\private_key”. 
Step 2 - Use PuTTYgen to convert the private key to PPK format
Vagrant stores the private key in a OpenSSH format. However PuTTY only supports keys that are in PPK format (PuTTY Private Key). So now we will have to convert the private key from OpenSSH format to PPK format.There is a tool called PuTTYgen to do this. The steps to be followed are given below.
(Note: You can optionally choose a passphrase for your private key. I am not doing so because I am just running a home lab here.)
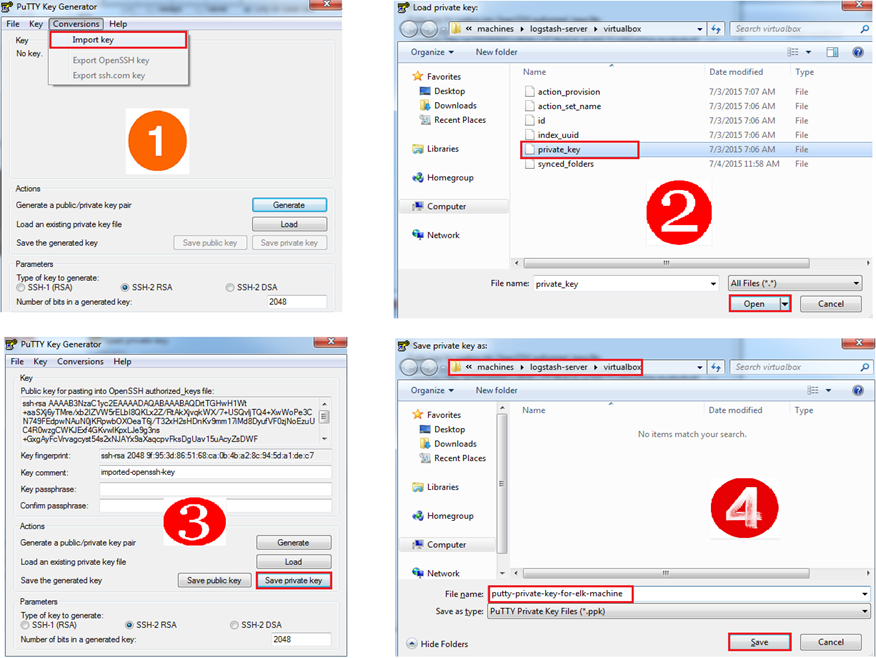
Step 3 - Configure PuTTY to use the private key
Now that you have the private key in PPK format, configure PuTTY to use the same: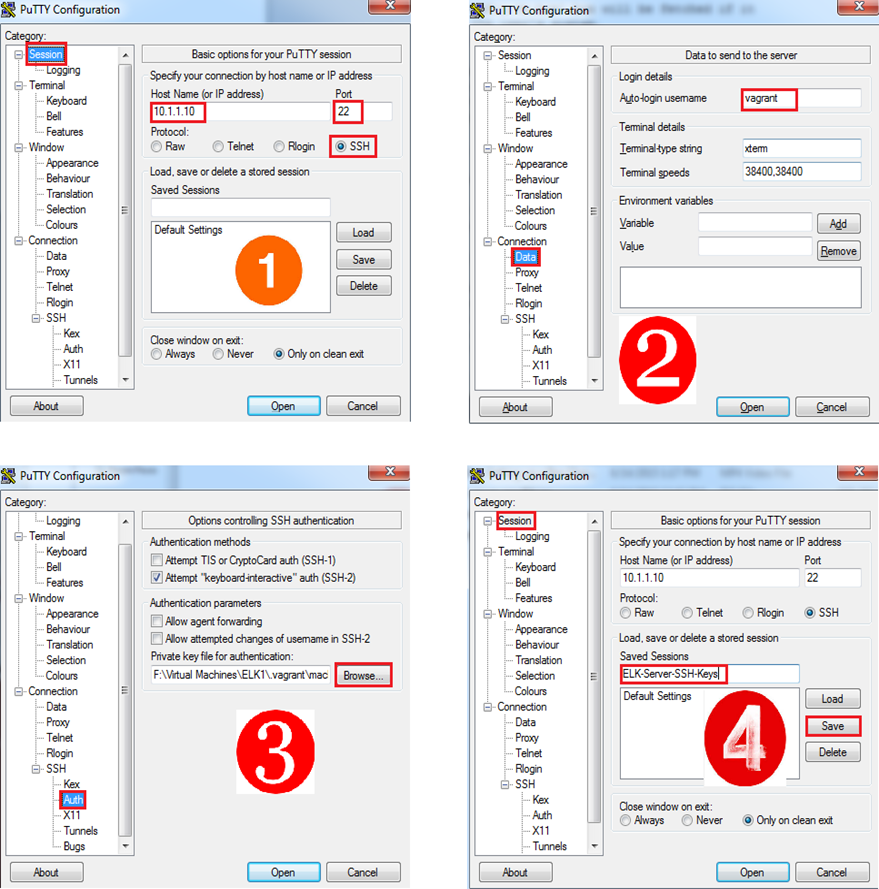
Step 4 - Just connect!
Everything done right, you can now use PuTTY to connect directly to your Vagrant VM without any username and password!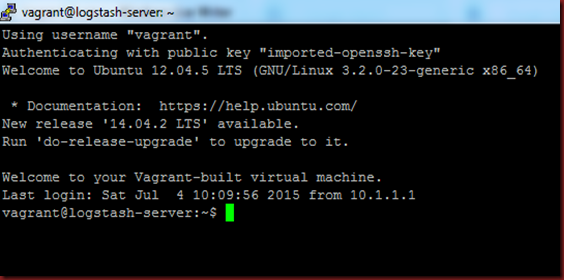
Thank you Sir for this! :)
ReplyDeletecan you make tutorial for winSCP?
thank you so much! :)
Thanks. This really helps. :)
ReplyDeleteThank you
ReplyDelete