In the previous article I covered how you can choose the right instances according to your purpose. Once you have chosen the instances it’s time to understand the configuration options available to you. I use the acronym KITS to refer to instance configuration options. This is in no way comprehensive but covers the minimum portion of what you need to know.
- K (Key Pairs)
- I (IP Addresses)
- T (Tags)
- S (Security Groups)
#1 - Key Pairs
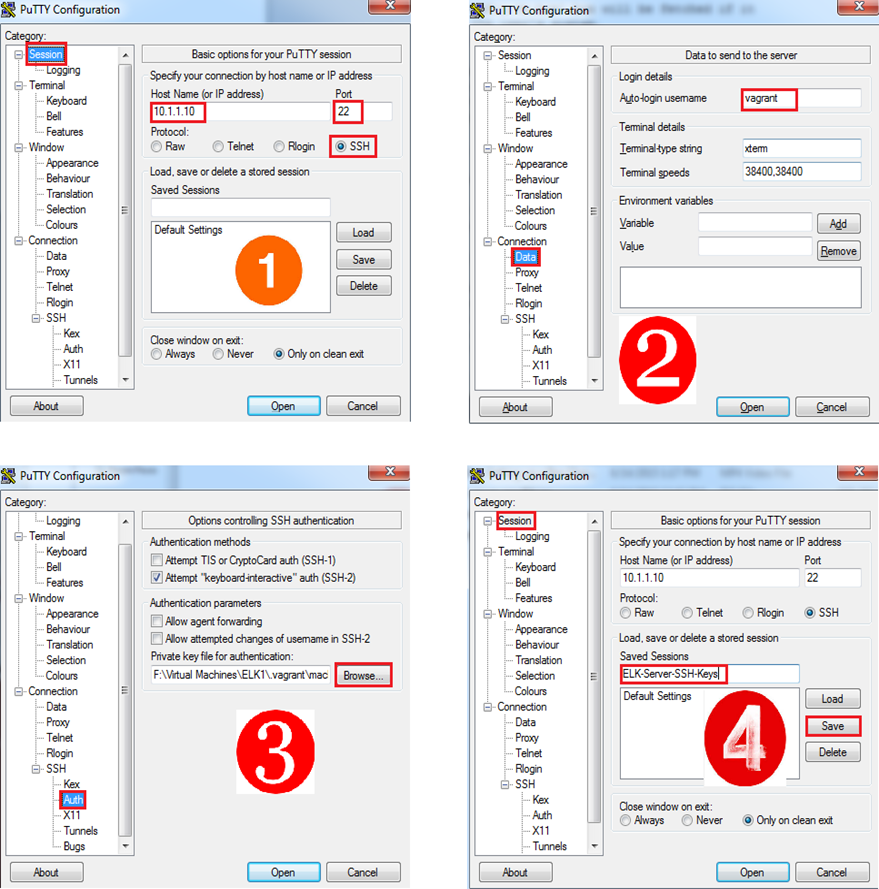
After you create an instance, how do you connect to it? In the AWS world, you need a couple of things to connect to an instance – IP Address and Key Pairs. We shall look at Key Pairs in this section and IP addresses in the next.
How do Key Pairs work?
To understand Key Pairs we’ll take the example of Alice and Bob who want to communicate securely over email. That is, even if someone intercepts the emails in transit he should not be able to make sense of the contents of the mail. To accomplish this, they use an email program called PGP. This is how it works: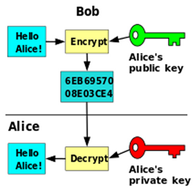
- Alice uses PGP to generate her own public and private key. This set of keys is called a Key Pair. The keys are generated and stored as text files.
- Alice keeps the private key to herself and distributes her public key to Bob.
- When Bob wants to send a message to Alice, he loads Alice’s public key into his PGP program. PGP then uses this key and encrypts Bob’s message.
- This message can now be decrypted only by someone who has Alice’s private key – which (hopefully) should be only Alice. So on receipt of Bob’s message, the PGP program running on Alice’s machine decrypts the message using Alice’s private key and gives the clear text message “Hello Alice!”.
In summary, a Key Pair consists of a couple of keys called public and private key. Any information encrypted using the public key can ONLY be decrypted with the private key (and vice-versa).
Now let’s see how these Key pairs are used in AWS.
How are Key pairs used in a Linux instance?
Most of the Linux distributions provide support for a cryptographic protocol called Secure Shell (SSH). SSH is client-server based and allows a user to remotely logon to a Linux system using public/private Key Pairs.
When you want to connect to an EC2 Linux instance, the following things are required:
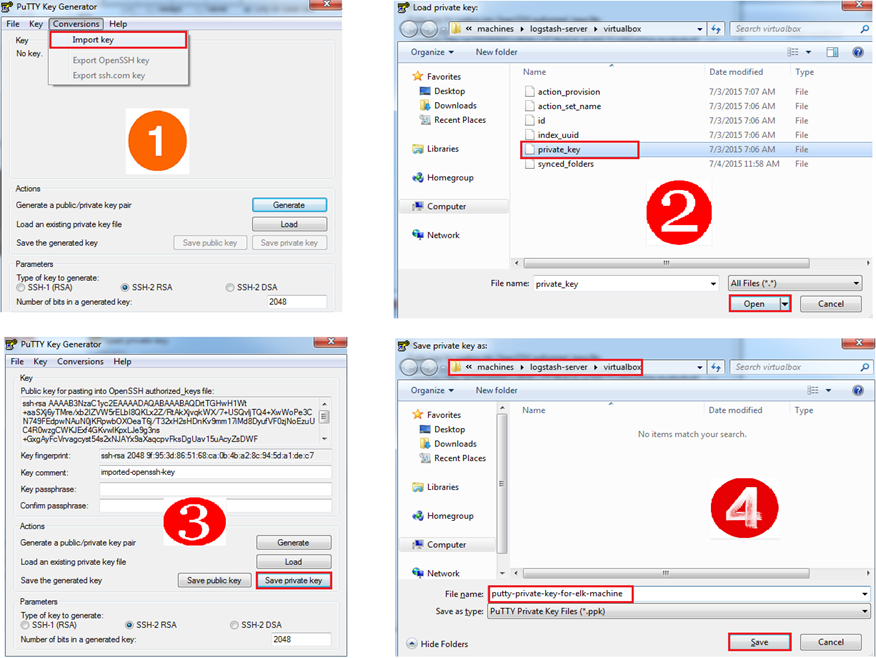
- A public-private key pair - This key-pair can be created by AWS itself or using tools like ssh-keygen or PuTTYgen.
- The SSH package – This is available by default on most Linux instances.
- The sshd service – This service is the “server” side SSH. It should be running on the instance when it boots up.
- The authorized_hosts file on the Linux instance must have the public key added to it.
- SSH client – The “client” side of SSH. There are lots of SSH clients available out there. I usually go with PuTTY. The private key must be available with the SSH client to automatically connect to the instance (without using any passwords).
Steps 1 to 4 will typically be taken care by AWS when you bring up an instance.
How are Key pairs used in a Windows instance?
Windows does not support SSH out-of-the-box. So the public-private keys are used in a different way here. The pre-requisites for Windows are:
- A public-private key pair - This key-pair can be created by AWS itself or using tools like ssh-keygen or PuTTYgen.
- A Windows user account – When you install Windows it automatically creates an Administrator user.
- The user account’s password – This will be automatically set by AWS. The password will then be encrypted with the public key. Remember that the password encrypted with the public key can ONLY be decrypted with the private key.
- The private key – Will be required to decrypt the password. Loading the private key and decrypting the password can be done via AWS console itself.
- A Remote Desktop (RDP) Client - Once you have the password you can use an RDP client and logon to the Windows machine. Here again you have a number of options. I normally use Remote Desktop Services (mstsc) that comes default with Windows.
Steps 1 to 3 will be done automatically by AWS when you bring up an instance.
#2 - IP Addresses
http://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/vpc-ip-addressing.html
What is a VPC?
When talking about IP addresses it’s important to understand a bit about VPC (or) Virtual Private Cloud. A VPC is like a "network container" for your AWS instances. Inside this container you can create your own subnets, assign routes, setup internet gateways, and even create a VPN tunnel to your premises. VPC is just Amazon’s way of making network administrators feel at home when they are configuring cloud instances:)
When you login to your AWS account, you will find that there is a default VPC already created for any region that you select. This is just to make launching instances easier if you don’t want to get into the nitty-gritties of configuring the network. However, you can create your own VPCs in addition to the default one. A region can have a maximum of 5 VPCs. Also, you cannot create a VPC larger than /16.
To explain VPC in a better way take a look at the below example:

What types of IP Addresses exist?
Private IP Address
Private IP addresses are not routable to the internet. The list of these IP addresses are (as per RFC 1918):
10.0.0.0 to 10.255.255.255 (or) 10.0.0.0/8
172.16.0.0 to 172.31.255.255 (or) 172.16.0.0/12
192.168.0.0 to 192.168.255.255 (or) 192.168.0.0/16
Every EC2 instance gets a Private IP assigned to it by default. This is called the Primary Private IP address.
Public IP Address
A public IP address makes an instance accessible from the internet. If you configure an instance with a default subnet then it is automatically assigned a public IP. You can also explicitly override assigning a public IP when launching an instance.
Elastic IP Address
Let’s say your instance has a public IP assigned to it. What happens when you shutdown or restart the instance? You will be assigned a new Public IP from the EC2-VPC public IP address pool. Now this can be a problem especially if you are hosting a website on that IP address.
A solution to this problem is to use what is called an Elastic IP or EIP. An EIP is basically a public IP address that you can tie to an instance. You can also untie it from a running instance and reassign it to another instance. For more specifics on EIP refer AWS documentation.
Note: If you have Elastic IP tied to an instance and the instance is not running then you will be charged for it.This is AWS’ way of ensuring efficient usage of public IP addresses!
#3 – Tags
After Key Pairs and IP Addresses it’s time to move to something easier. It’s time for Tags!
Tags are case-sensitive key/value pairs that you can add to an instance. One instance can have up to 10 tags associated with it. Tags can be useful to:
- Group and Manage Instances
- Instance Usage Report based on tag keys
- Get AWS account bill based on tag keys
You can read more about tags from here.
#4 - Security Groups
A Security Group (SG) is a collection of network access rules. Using SGs you can define Ports, Protocols and Hosts that are allowed to interact with your EC2 instance. A few examples are - “Allow only ICMP Echo Requests”, “Allow SSH traffic only from 192.168.1.1”, “Allow outbound TCP connections over port 80” and so on. You can attach multiple Security Groups to one instance.
An important limitation of Security Groups is that you can only filter allow traffic and not deny traffic. For example, if you want to block a list of known malicious IPs then you cannot do it using Security Groups.
One solution would be to control deny traffic via host based controls like iptables for Linux and WFAS for Windows. Alternately, AWS also provides something called as NACL (Network Access Control Lists) that can help you with deny traffic. A comparison of NACL and Security groups is given here.
AWS currently places the following limits when configuring SGs:
- Only 100 Security Groups are allowed per VPC
- Each Security Group can have up to 50 Rules
- A Network Interface can be assigned to a maximum of 5 Security Groups
For more information on Securing the VPC refer AWS Documentation.
Now that you understand the LAMPS and the KITS, you can be more confident in bringing up your instance in AWS. If you are creating a multi-tiered/clustered environment it helps to explore more on VPC. Thanks for reading!